The conversation around privacy in artificial intelligence has shifted from “how do we secure stored data?” to “how do we secure data while it is being used?” This is where homomorphic encryption for machine learning enters the picture. Instead of decrypting sensitive information before analysis, this cryptographic approach allows algorithms to operate directly on encrypted data.
The result is usable output that only the data owner can unlock. For organizations handling medical records, financial transactions, or proprietary research, this approach offers a path to analytics and prediction without surrendering confidentiality.
For years, data security strategies focused on encryption at rest and encryption in transit. Yet once data reached a processing server, it often had to be decrypted, exposing it to internal threats, misconfigurations, or breaches.
Homomorphic encryption shifts that paradigm. It introduces the possibility of encrypted computation, where data remains concealed even during complex operations such as model inference or collaborative training. This change is not theoretical anymore; it is steadily moving into practical deployments across industries that rely on machine learning.
Understanding the Foundations of Homomorphic Encryption for Machine Learning
Homomorphic encryption is not a single algorithm but a family of cryptographic schemes designed to support mathematical operations on ciphertext. When decrypted, the result mirrors what would have been obtained if the same operations had been performed on the original plaintext. In machine learning, this enables tasks like classification, regression, or recommendation generation without revealing the underlying input data to the computing party.
There are different levels of homomorphic capability. Some schemes allow only addition, others allow both addition and multiplication but with limits, and fully homomorphic encryption supports arbitrary computations.
Machine learning models typically rely heavily on multiplication and addition, especially in linear algebra and neural network layers. As a result, modern implementations often lean on schemes that balance computational flexibility with performance, such as those supporting approximate arithmetic suited to floating-point operations.
A helpful way to picture this is to imagine sending a locked box to a service provider. Instead of opening the box, the provider manipulates it through a special mechanism that preserves its locked state. When the box returns, the owner unlocks it and finds the processed result inside. The provider never sees the contents, yet the task is completed correctly.
Designing Secure AI Pipelines with Homomorphic Encryption for Machine Learning
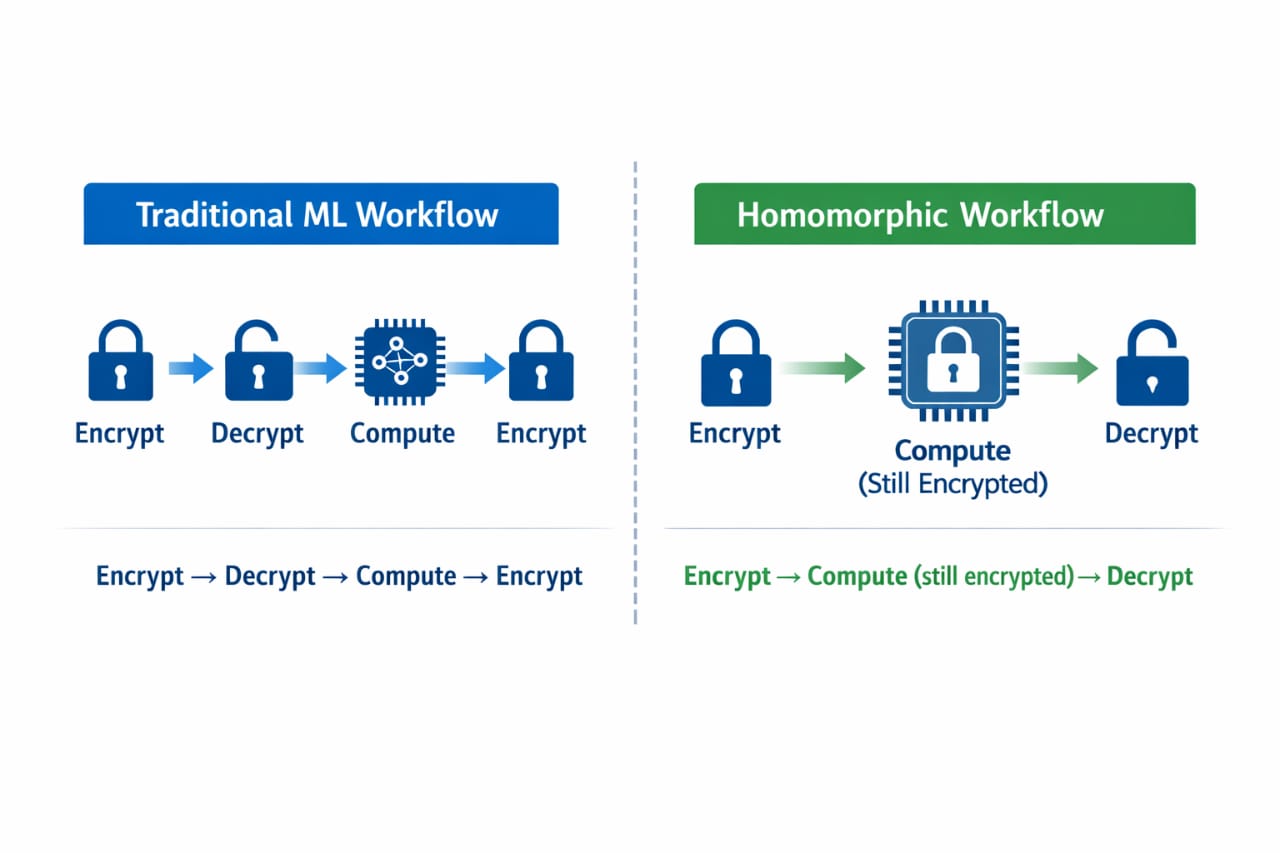
A secure machine learning workflow using homomorphic encryption typically begins on the client side.
Data owners encrypt their datasets locally using a public key before transmission. Once encrypted, the data can be stored, shared, or processed in external environments such as cloud platforms without exposing raw values. The service performing the computation does not possess the private key required to decrypt the information.
During computation, the encrypted data undergoes mathematical transformations that mirror traditional model operations. Linear layers, aggregations, and certain nonlinear approximations can be executed directly on ciphertext. After processing, the encrypted result is returned to the data owner, who decrypts it to obtain the prediction or analytical output.
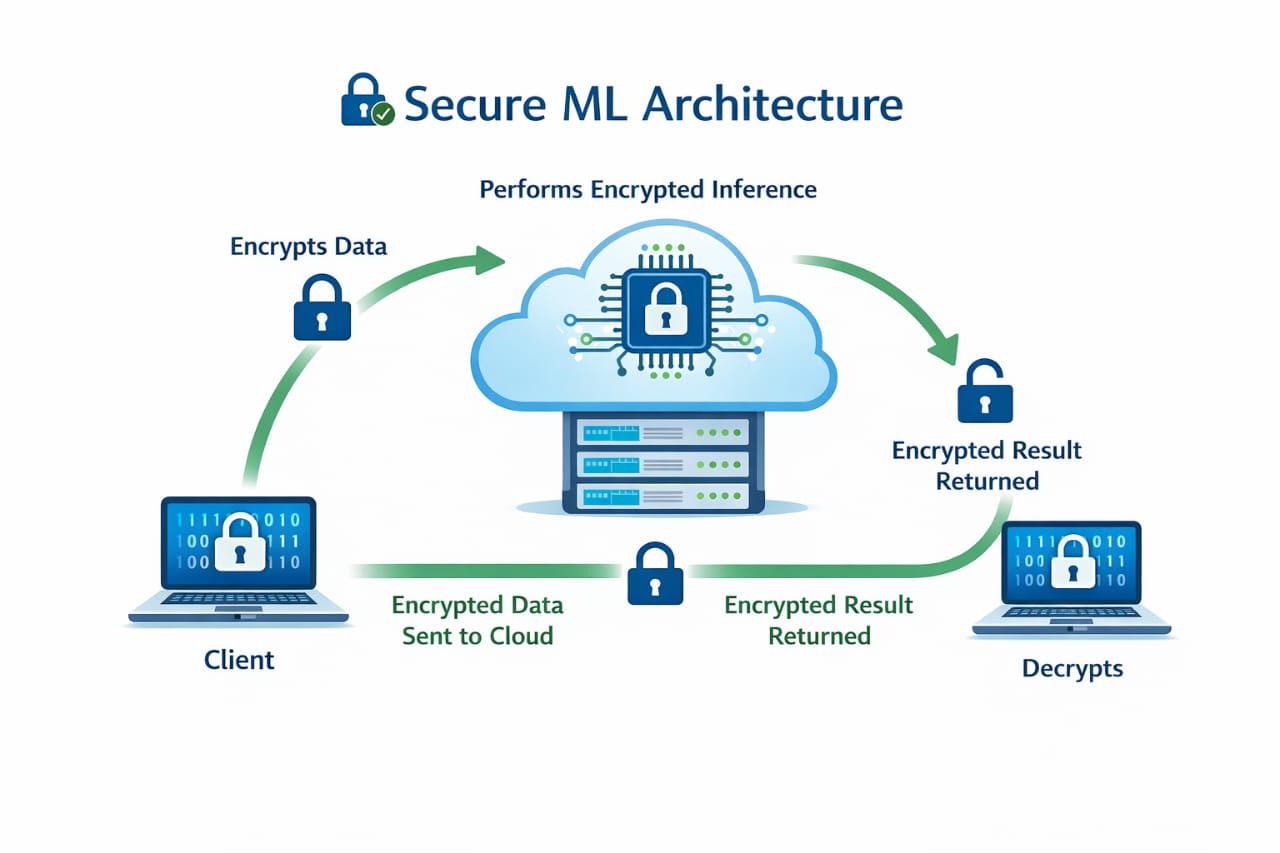
This design supports several practical scenarios. A hospital could use an external AI service to analyze patient scans without transferring identifiable information in readable form.
A financial institution might evaluate credit risk models on encrypted customer data while keeping personal details concealed. Research collaborations between institutions can also benefit, allowing joint model training without sharing raw datasets.
Performance Realities and Engineering Trade-Offs
Despite its promise, homomorphic encryption introduces computational overhead that engineers must account for. Operations on encrypted data are significantly heavier than their plaintext equivalents. Ciphertexts are larger in size, and arithmetic operations require more processing time and memory. These constraints influence how models are designed and deployed.
To manage this overhead, practitioners often adopt optimization strategies. One approach involves packing multiple data points into a single ciphertext so that a single operation processes many values simultaneously.
Another strategy replaces certain nonlinear activation functions with polynomial approximations that are more compatible with encrypted arithmetic. These adjustments help maintain acceptable performance while preserving privacy.
There is also the concept of “noise” in homomorphic encryption. Each encrypted operation adds a small amount of mathematical distortion that accumulates over time. If this noise grows beyond a threshold, the ciphertext becomes undecipherable. Advanced schemes include techniques such as bootstrapping to refresh ciphertexts and reduce accumulated noise, though this process itself is computationally expensive. Engineers must balance model depth, accuracy, and processing time when designing encrypted workflows.
Practical Tools and Development Ecosystem
The growing ecosystem of libraries and frameworks has lowered the barrier to experimentation and adoption. Several open-source toolkits provide implementations of popular encryption schemes along with utilities for batching operations, managing keys, and integrating with common programming languages. Some platforms also offer compilers that translate conventional machine learning models into encrypted circuits, reducing the need for manual cryptographic expertise.
These tools are steadily improving usability and documentation, which is critical for broader adoption.
Developers can now prototype encrypted inference systems using familiar languages such as Python or C++ and gradually scale toward production environments. While expertise in cryptography remains valuable, it is no longer a strict prerequisite for entry.
Industry participation has also expanded. Technology companies, academic institutions, and research labs continue to publish performance benchmarks and architectural guidelines. This collaborative momentum helps validate claims, surface limitations, and guide realistic expectations for deployment.
Real-World Applications Across Industries
Healthcare stands out as a natural beneficiary. Patient data is both highly sensitive and immensely valuable for predictive analytics. Homomorphic encryption enables external model evaluation or cross-institutional studies without revealing personal identifiers.
In finance, encrypted analytics can support fraud detection and credit scoring while respecting strict data protection regulations. Government agencies exploring secure data sharing also see potential in encrypted computation for policy research and interdepartmental collaboration.
Another emerging area is encrypted model inference for consumer applications. Users could submit encrypted queries to recommendation systems or search engines and receive encrypted responses that only their devices can decode. This approach reduces the exposure of personal behavior patterns while still delivering personalized experiences.
These applications illustrate a gradual shift from centralized data ownership toward privacy-preserving collaboration. Rather than concentrating sensitive information in a single location, organizations can distribute computation while keeping raw data concealed.
Limitations, Risks, and Responsible Expectations
Homomorphic encryption is not a universal solution. The computational demands can be prohibitive for large-scale deep learning models or real-time analytics with strict latency requirements. Some tasks may still be better served by complementary techniques such as secure multi-party computation, differential privacy, or trusted execution environments. Each method addresses privacy from a different angle, and hybrid approaches often deliver the most practical balance.
There are also operational considerations. Key management becomes crucial because losing a private key renders encrypted results permanently inaccessible. Implementation errors, performance miscalculations, or unrealistic expectations can undermine the benefits. Responsible adoption requires careful planning, testing, and transparent communication about capabilities and limits.
From an expertise perspective, teams benefit from interdisciplinary collaboration. Cryptographers, machine learning engineers, and infrastructure specialists each contribute insights that shape a workable system. This collaborative model aligns with strong engineering governance and helps maintain both security and functionality.
What Lies Ahead for Encrypted Machine Learning
Research continues to focus on improving efficiency, reducing ciphertext size, and accelerating bootstrapping operations. Advances in hardware acceleration, parallel processing, and compiler design are gradually closing the performance gap between encrypted and plaintext computation. While encrypted workflows will likely remain heavier than traditional pipelines, the difference is shrinking with each generation of innovation.
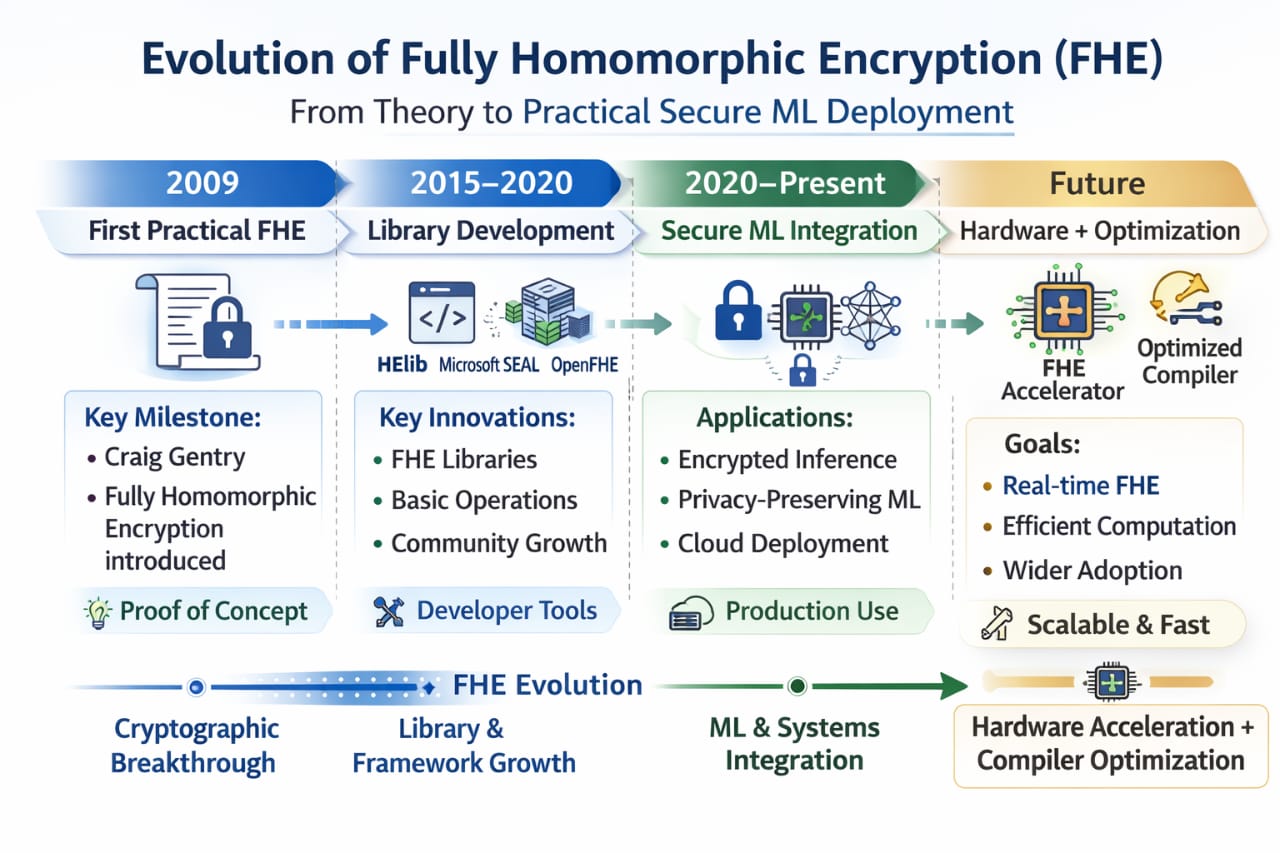
Equally important is the cultural shift in how organizations view data access. Instead of treating encryption solely as a defensive layer, homomorphic approaches encourage a proactive design mindset where privacy is embedded into computational logic from the beginning. This perspective aligns with evolving regulatory frameworks and growing public awareness of data protection.
Homomorphic encryption for machine learning represents a significant step toward analytics that respect confidentiality without sacrificing utility. It does not eliminate all privacy challenges, nor does it replace every existing security technique. What it offers is a credible pathway to perform meaningful computation while keeping sensitive information concealed throughout the entire lifecycle of data processing.
Discover more from Aree Blog
Subscribe now to keep reading and get access to the full archive.